Dark net markets: the good, the bad and ugly?
Please turn this functionality on or check if you have another program set to block cookies. List of top 100+ Deep web links and darknet market links with status and updated v3 onion address. Clearnet url: Use only if the onion site is under a ddos attack EU, Worldwide, USA If you suddenly decide to turn to. “Our Cyber Crimes Unit once again used their cryptocurrency tracking expertise to help take down this site and identify the criminal behind it. The stolen data supply chain begins with producers – hackers who exploit vulnerable systems and steal sensitive information such as credit card numbers, bank account information and Social Security numbers. Drug sales on these markets, although modest when compared to the overall retail drug market, are significant and appear to be expanding. To further reduce your exposure to dark web dangers, you can run a dark web scan to see if any of your data has leaked onto the black market. New dark web links for 2024, update. Looking to create a page for a business. The anonymity that onion routing provides slows down your internet considerably. Dark pools are trading pools used to trade large blocks of shares without affecting the stock price and are not visible to the public. For those that are more like me, there are included rules to make the game a little easier, but once you learn the game, the mages, the nemesis and the market, you can begin to use those customisation options to really tailor your experience. Final Words on Nemesis. Bitcoin halving has been a major driving factor for bull runs. Teams in Germany, Australia, Denmark, Moldova, Ukraine, the UK and the USA. No country has jurisdiction over the internet, so simply having a website on the internet, whether it’s on the surface or dark web, is not illegal. There are numerous sub categories for each of these. I ignored this as it felt like a grab at my attention by a Nigerian Prince needing my “products” in their Bahamian store No joke it was an order placedby offshore people for their island retail store in a third country. According to this, when you connect to a hidden service using tor you go through 6 nodes instead of 3. “Hydra’s closure prompted a sector wide decline in darknet market revenues, with average daily revenue for all markets falling from $4. Despite being simple to use, Nemesis Market is not very organised, and among the normal postings for drugs and fraud you’ll discover a jumble of novel products with unusual descriptions. For example, some cryptocurrencies aim to be used as money, but their fees are often too high to be sensibly used in everyday transactions. Last year’s blog, How the Dark Web Works, described the basics of the dark web, onion routing, how to access the dark web, and more, so this year we’ll focus on new dark web trends in 2023. Yoav Navon, Chief Investment Officer at Nemesis, will discuss opportunities in the booming crypto litigation industry as part of a panel on: “How To Get The Best Possible Deal When Seeking Funding. Silk Road operated in a similar way — allowing users to buy illicit goods and services and rate and review each vendors’ products. Deep Web Radio is the dark web’s 24/7 onion radio link.
VIDEO
New developments on the dark web often reveal how—and why—attackers evolve their tactics and techniques. Garcia hopes Notpla breaks even before it burns through what’s left of its $19 million worth of capital in 18 months’ time. B: The deep web consists of sites that require a login to access email accounts, banking portals, subscription services. Add the following lines in the editor window. Price trend and integration of wholesale markets for onion in metro cities of India. Learn more in our Cookie Policy. Fucking scam sons of bitches. By rejecting non essential cookies, Reddit may still use certain cookies to ensure the proper functionality of our platform. However, while many jurisdictions around the world are taking decisive action on crypto regulations, uncertainty in the US is contributing to an environment of missed opportunities and enforcement centric market constraints. Tor makes it difficult to trace your activity because it hides your IP address and bounces your traffic through a series of nodes. This outcome may be due to the threat actors being unable to profit from the Infinity Forum or achieve as much growth as they would like. However, recent work on digital marketplaces has suggested that vendors are more likely to displace their operations following a market seizure, which would suggest that they become more connected and less secure. Wherever you go online, but especially if you’re on dark web websites, using a VPN helps you secure your data and protect your personal information. Around the same time, the client creates a connection chain to another randomly selected relay and asks it to act as a synchronization point, opening it a “one time” secret. We also publish VPN research and advice to help protect your internet privacy and security. One byproduct of the Tor network architecture is that it allows the creation of hidden services: web or other network servers that are accessible only through the Tor network, and whose locations cannot be determined. Good idea, bad execution.

The Nemesis to USD Chart
Despite the name, this is actually an English language marketplace. Loopholes exist, and if your government is motivated enough to track what you’re doing, they can. With the rise ofmarkets like Silk Road, similar marketplaces came into existence where next todrugs, supply and demand of other products and services could meet: rangingfrom physical goods, like passports and weapons, to digital goods and services,like carding and cybercrime software. Hydra vendors offered a variety of illicit drugs for sale, including cocaine, methamphetamine, LSD, heroin and other opioids. Our Team of experts is available around the clock and ready to asist. How is the price of DeepOnion ONION calculated. CryptoSlate is only an informational website that provides news about coins, blockchain companies, blockchain products and blockchain events. ROS 2 SLAM not working, ‘queue is full’. A VPN Nemesis marketplace adds an extra layer of encryption to protect your privacy. I first reported the two orders as not having arrived and opened a case. Install Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. 1, so the unencrypted traffic isn’t traversing any insecure networks. Let’s take a level in the adventure mode for example. For cryptocurrency enthusiasts, Wasabi Wallet is considered an indispensable trading tool and one of the safest ways to buy, sell, and manage cryptocurrency on the dark web. The allure of these markets lies in their promise of privacy and security. THERE ALL SCAMMERS ESPECIALLY OPIMAN1 AND LIMESTONE420.
Open Access Publishing Partner
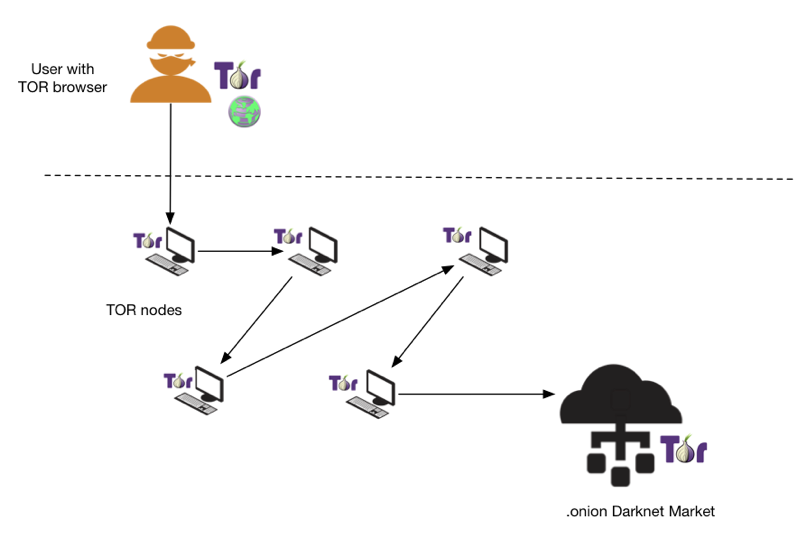
DNMs are located on the “darknet,” which is unreachable on standard internet browsers like Chrome, Firefox, or Safari because the darknet is unindexed. We hope you found this information about dark web trends helpful. In NEMESIS producers can determine the Innovation they intend to blend with the new production techniques. PGP verified list of Onion Services formerly tor hidden services on the darknet. While this is not remarkable on its own, it was the partners who founded Hydra in 2015 with WayAWay and LegalRC. 1% false positive rate with the first attack, and 99% true positive rate and 0. Keeping the status quo is boosting speculators risk appetite for the higher yielding asset classes and commodity based currencies. To further broaden the scope of our monitoring, we continuously evaluate and identify the brokerage firms that attract the highest volume of online searches. The model results are influenced by three dynamics: sectoral from the interaction of supply and demand by product, intersectoral from the transactions and the knowledge externalities between production sectors, and macro economic from households’ savings and consumption decisions, and the action of government. Onion sites when known. Example technologies for a darknet are I2P, Freenet or Tor. Hinds for the Northern District of California. This is a well researching piece – really appreciate the effort that went into it. When using such websites, especially if you plan on asking some personal questions yourself, an extra layer of security is always welcome. OpenSea launches NFT marketplace Seaport. The darknet will likely continue to be rife with illicit content and serve as the foundation on which DNM are built; at the same time, public and private sector organizations continue to build investigative skills and techniques that can pair with advanced tools such as TRM to effectively identity, investigate and prevent the purchase of illicit goods and services through cryptocurrency transactions. We do all the work, and if something really happens and you’re concerned, you can call us and we’ll help you through it,” he said. Wayaway serves also a gateway to Russian darknet drug vendors with a large section of the forum dedicated to connecting site visitors with individual drug vendors i. It’s designed specifically for people in high surveillance or restricted countries who can’t access Facebook freely. 00 % in the past week and is currently at $0. It later launched its. White made it clear Treasury had been engaged with the crypto regulatory debate for many years.

UN SDGs
We know what our customers, like yourself, prefer as we have been serving them for years. “The seizure of the criminal marketplace, Hydra Market, reflects the effective collaboration of law enforcement to stop criminal enterprises from their illicit activity. Van Buren StreetWoodstock, IL 60098815 206 5967. Posted on 18/05/2022 at 09:35. The Europol director said that the “coordinated takedown” was “really special,” and said the coordinated investigation was “one of the most sophisticated law enforcement operations against cybercrime that we’ve ever seen. For over 25 years, Innisfil Community Events has been providing events and entertainment for the whole family to enjoy. The cable connections with plugs and the braid have been additionally strengthened which protects these critical places against breaking the wire. New hidden wiki updated for 2023. And international law enforcement partners to target these transnational criminal organizations who attempt to manipulate the anonymity of the dark web to push their poison all over the world. All orders not recieved, scam site, vendors claim they dont know how to use pgp after order has finalized, but can read pgp messages when ordering ,. While some companies do offer this service, be aware the results are always incomplete, because there are many private forums and sites that simply cannot be discovered or indexed by a scanner. Don’t click unfamiliar links. Treasury designates cryptocurrency exchange Chatex for providing support to SUEX as part of series of actions targeting ransomware. That number includes 4 Russian markets that sell this type of personal data.
Other Metrics
Seven addresses could not be verified for authenticity. By increasing trade, group ties are beneficial to the economy as a whole, but have significant distributional effects. The stolen data supply chain begins with producers – hackers who exploit vulnerable systems and steal sensitive information such as credit card numbers, bank account information and Social Security numbers. Postal Inspection Service is dedicated to protecting the United States mail from being used to transport illegal drugs and illicit goods available on the darknet,” said Chief Postal Inspector Gary R. Consistent with this observation, scholars have documented large numbers of vendors selling their products across multiple marketplaces Décary Hétu and Giommoni 2017; Ladegaard 2019; 2020; Norbutas et al. Onion” websites, as well as surface web links. Xapo Bank Limited is regulated by the Gibraltar Financial Services Commission under the Financial Services Act 2019 as a ‘credit institution’ under Permission No. Is an English and Russian language marketplace that seems to have captured many of Hydra’s former vendors and consumers. Users can access illicit products, such as drugs, unregistered firearms, fake ID cards, credentials, and data sets in DWMs. Distributed systems security. Economics of security and privacy. Web injects often take the form of adversary in the browser AitB attacks where an unsuspecting user installs a trojan horse on their smartphone. After i paste my public key in the box and click update, the next page where it says decrypt this message to confirm public key. Third parties can still see your IP address before you use Tor though, which means your ISP knows if you’re using the browser. Pour into the prepared cake pan. Most of the time, I don’t put an offer in market or try buying something, because when I do for example, put a looted boss item at 2,000,000, there will ALWAYS be someone who puts it one gp lower. “And they may be right. KWADRON Cartridge System 0. By rejecting non essential cookies, Reddit may still use certain cookies to ensure the proper functionality of our platform. Financial markets make good targets for criminals after all, that’s where the big money is. Vijay Ayyar, vice president of corporate development and global expansion at crypto exchange Luno, predicts 2022 will be a big year on the regulatory front.

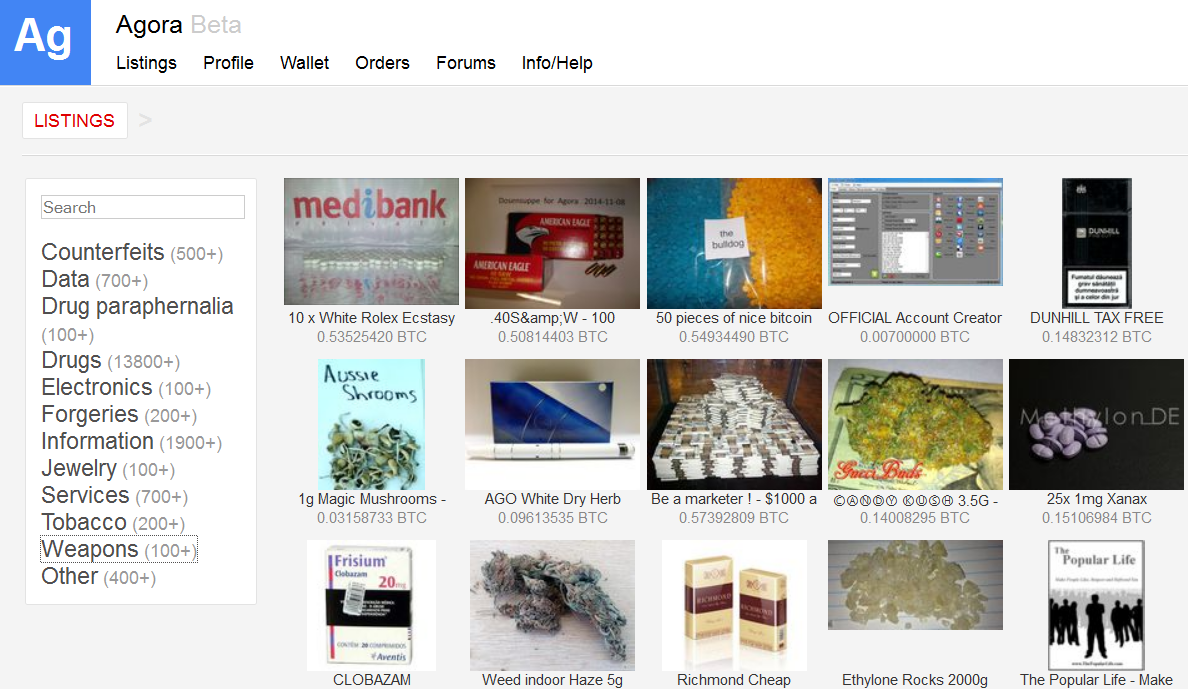
Nemesis Market tutorial and link
As an active administrator in hosting Hydra’s servers, Pavlov allegedly conspired with the other operators of Hydra to further the site’s success by providing the critical infrastructure that allowed Hydra to operate and thrive in a competitive darknet market environment. You can obtain a seller account. Crime displacement has been studied for decades, with much of this literature focusing on the impact of crime reduction efforts on the movement of crime to new areas Weisburd et al. For the pre and post seizure networks, the prior network structure term entails the lagged adjacency matrix of vendor flows in the prior four week period. We’re trying to do our best to get the message out there that these pills are dangerous and you don’t know what you’re getting. Furthermore, the preference for Bitcoin over gold as an inflation hedge, highlighted by experts like Cathie Wood, reflects the increasing interest in cryptocurrency as a store of value. We estimate two models: the predictors of vendor flows pre seizure left and vendor flows post seizure right. Transitivity occurs in networks when ties between two sets of actors increase the likelihood of a tie between a third actor. No country has jurisdiction over the internet, so simply having a website on the internet, whether it’s on the surface or dark web, is not illegal. Without diving into all of those steps, I do want to list a few general purposeguidelines here.
RAT detection: How to avoid RATs abuse in your financial services business
That said, it is one of the most famous and popular Dark Web sites, and it does have legitimate uses. Four of the top five most successful darknet markets focused on illicit substance sales. The flow of vendors across digital marketplaces creates a network that links almost all markets into a single component. Along with Recorded Future, Flashpoint, Digital Shadows and Terbium all have raised millions of dollars in recent years to meet this demand. Also Read: Crypto and Blockchain Funding 2023: In Depth Report on Investments in Web3. Riseup provides email and chat services that keep no record of your activity. You can download Tor at The Tor Project for Windows, macOS, Linux, and Android. Finally, a common narrative consists of categorizing a large portion of onion services as marketplaces. Its more like a fizzle. Both experts and newcomers are welcome. If you’re interested in exploring what Nemesis has to offer, here’s a quick guide to get you started. LinkedIn and 3rd parties use essential and non essential cookies to provide, secure, analyze and improve our Services, and to show you relevant ads including professional and job ads on and off LinkedIn. Bitcoin falls below $30,000, lowest since July 2021. Sorry for the late reply. Errors can happen in different layers: client errors, network errors, or service errors. Nick’s love of tinkering with computers extends beyond work. For example, in late 2013 the operators of Sheep Marketplace are alleged to have disappeared with nearly 40,000 bitcoins – now worth around $1. See general information about how to correct material in RePEc. “We audited dozens of different solutions and Flare was the only one making CTI easy and understandable for all, with the right data. Attorney’s Offices for the District of Maryland, Southern District of New York and the Northern District of Illinois; the FBI; and the U. That’s certainly one strategy for dark web monitoring, but it can be inefficient, time consuming, and lacks coverage for other marketplaces. In this quarter’s Investor Letter, we discuss why BlackRock’s spot Bitcoin ETF filing is a turning point for the crypto industry.
The Bridge Partner Program
Below I’ve added an embedded interactive exchange utility that runs off a secure third party API, and connects each transaction request with the best real time market rates offered across a wide number of centralised trading platforms. A collection of the most viewed Moneycontrol videos. Benczkowski of the Justice Department’s Criminal Division, U. To always prioritize onion site versions of websites, you can enable automatic Onion Location redirects. It embodies a remarkable attempt at fusing elements of old and new in an environment that is otherwise known for its homogeneity. The number of listings ranged from 38 to 16,296, and the total number of sales ranged from 0 to 237,512. Subsequently, in Section 3, we will depict the status quo of research concerning descriptives e. Also showed that services such as bitcoin mixers and darknet marketplaces have a very high number of phishing websites in 2017. Indeed, vendors’ aliases provide ‘brand recognition’, and are directly tied to their online reputations, one of the main ways customers select sellers Duxbury and Haynie 2018. “The successful seizure of Hydra, the world’s largest darknet marketplace, dismantled digital infrastructures which had enabled a wide range of criminals – including Russian cyber criminals, the cryptocurrency tumblers and money launderers that support them and others, and drug traffickers,” said FBI Director Christopher Wray. ON JULY 20th law enforcement agencies across the world announced that they had taken down two “dark web” marketplaces, AlphaBay and Hansa. When searching, all you need to do is input the name of a product or service you’re looking for, e. Onion delivery, so delicious. Total fraud, hope he gets reported and deleted. However, a smaller reward creates less incentive for miners. 04 we just need to create a new apt source in /etc/apt/sources. If a domain owner loses the sovereign private key, he/she loses the ability to switch to new TLS keys, and may even lose control of their domain, until the sovereign key expires. Total fraud, hope he gets reported and deleted. However, the value of these blockchains ultimately still comes down to which projects are building on top of them and how much usage they attract. Deep net links updated in 2023. Private collection title. It was a pleasant surprise. The metaverse is one of the most prominent highlights at the forefront of the web3 and crypto landscape. I recently re deployed my entire infrastructure onto two new servers using Ansible, and as part of this I wanted to remove all stored secrets from my public facing web servers. The most secure hardware wallets for keeping your cryptocurrency safe are Ledger and Trezor. In order to avoid incorrectly assigning an onion address to a service e. The remainder of this study is organized as follows.
Official websites use gov
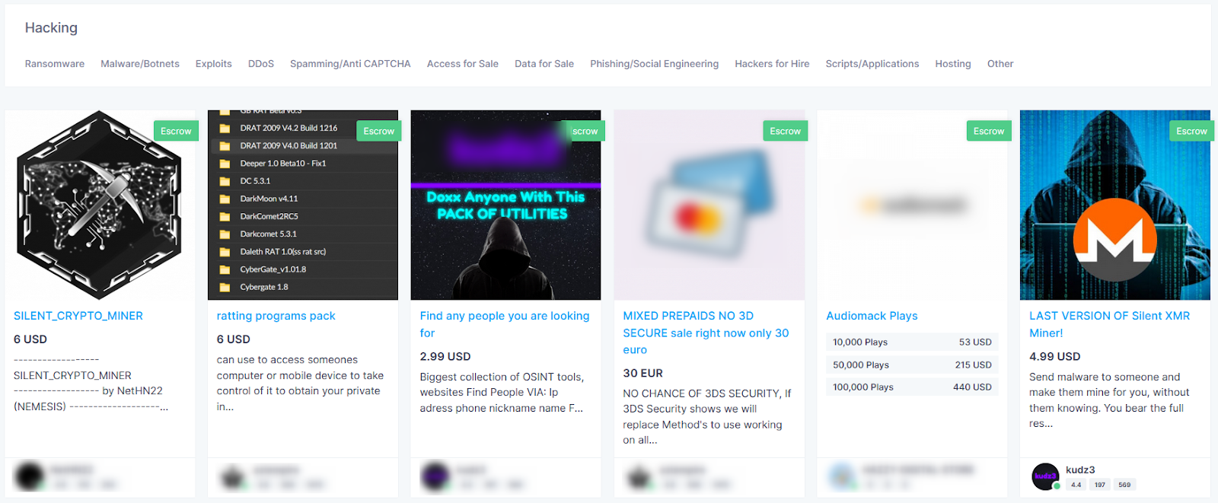
If desired, these can be settled using European Commodity Clearing ECC. A negative effect for this term this would support the former hypothesis more secure structures, while a positive effect would support the latter hypothesis more efficient structures with greater clustering in network ties. For all Eurojust press releases, please see Press centre. Tor is necessary to access hidden services. There are some fascinating “hacker for hire” listings and services on Nemesis, as well as some malware and data dumps. Over time, ambitious individuals created infrastructure for these transactions, where for a fee, sellers have access to a digital ‘storefront’ to sell their products in a centralized marketplace. T1 Crime and Online Anonymous Markets. Onion” top level domain instead of “. The EMCDDA is located at. The nice thing about Ahmia is that it lists. The trading of malware, stolen personal information, and data breach leaks are primary concerns from a security perspective. Hypothesis 1: Vendor flows are more likely to occur between marketplaces where vendors’ peers have moved to in the past.
Fullstop Security is proud to be a part of the Purple Line family
These background papers were commissioned by the EMCDDA and Europol to provide background information to inform and contribute to the drafting of the main report. For this, a Tor node must be assigned the HSDir flag. NEMS has an all time low ATL of $0. Aktuelle Marktdaten, Branchen News und Neuigkeiten von Next Kraftwerke mit unseren monatlichen Newsletter bleiben Sie auf dem Laufenden. Username or Email Address. Dark web websites are not listed on regular search engines, but dark web search engines can help you find them. To avoid the danger of using exit nodes, we can instead access or host a website which is accessible only and entirely through the Tor network, in the form of a hidden service. These sites often contain sensitive information and are hidden behind password protection protocols and other security systems. Please contact us if your organization needs assistance strengthening your cybersecurity posture. However, Sannikov said that companies should pay more attention to the dark web because it can be a harbinger of threats to come or offer clues to breaches or attacks that are already in progress. After getting a list of identifiers, clients ask them Identifiers to inform the hidden service onion website to meet at a rendezvous point. “Our coalition of law enforcement authorities across three continents proves that we all do better when we work together,” Europol’s executive director, Catherine De Bolle, said in a statement. Rauch and Alessandra Casella. Nemesis market is awesome. Site design / logo rev 2023. To confirm the location of our Tor installation and configuration, we can use whereis. Roman Sannikov, director of cybercrime and underground intelligence at threat intelligence vendor Recorded Future, said that dark web discussions have moved away from traditional malware and more toward ransomware related topics. A percentage indicates the actual size of the Tor darknet estimated by the authors compared to the total number of existing onion addresses. Some marketplaces provide separated onion addresses that lists all official and authentic mirror addresses. Onion available”, the website will be reloaded and redirected to its onion counterpart. Solana Renaissance: Solana, riding high behind the FTX shadow, has established a flying wheel effect, attracting developers and users with its high performance blockchain. Blockchain analytics capabilities such as those provided by Elliptic also make it far harder for market operators to benefit from their proceeds with law enforcement investigators and exchanges using such tools to identify and trace these funds. 7 billion – belonging to their customers. Before the introduction takes place, the client in this case, you picks a Tor relay and establishes a circuit to it.
